Tunnel definitions are not used, but rather an encryption policy based on access control lists is pushed down to each node from a central server. Data encryption is “on-demand” and is only applied to traffic that meets the specification of the access control lists.
Like tunnel-based VPNs, tunnel-less GET-VPN also encrypts the entire packet, but instead of generating a new header it recycles the original IP information. This “header preservation” takes advantage of the existing core routing structure for endpoint reachability, and eliminates the need for overlaid tunnels, preserves native Quality of Service support, and provides an efficient means for any-to-any (full-mesh) connectivity and for encrypted multicast replication.
GET VPN Components
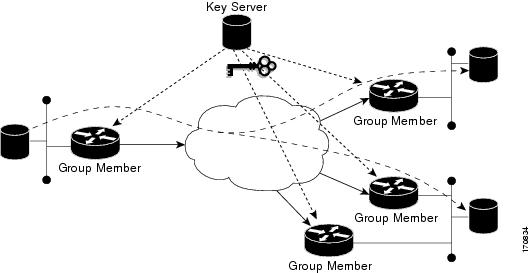
It is responsible for accepting or rejecting members into the VPN, generating/regenerating and distributing the encryption keys, and deploying the encryption policies to all of the registered Group Members.
A single Key Server is required, but multiple Key Servers can be deployed and is recommended to provide redundancy and load balancing since the encryption function of the VPN is dependent entirely upon the availability of the Key Server.
Group Member
Group Members are the individual node devices that protect local networks and encrypt traffic based on the encryption policy provided by the Key Server.
GDOI Group
The GET-VPN concept is based upon a “trusted group” model whose members employ a common security methodology. The GDOI group configuration, specified on the Key Server, contains the parameters needed to establish and maintain encryption policies between Group Members.
Identity
The identity number is a unique value that differentiates GDOI groups configured on a Key Server. No two groups can have the same identity number. The identity number determines which group the Group Member registers to.
Rekeying
In order to prevent service outages, GET-VPN initiates unicast rekeying events a minimum of 90 seconds prior to the expiration of the existing keys. The Key Server uses several parameters to attempt to estimate more accurately when to begin the rekeying process.
In addition to the TEK and KEK lifetime parameters, the Key Server uses the rekey retransmit number and time settings, and assumes a constant rekey processing time of 5 seconds per 50 Group Members.
With unicast rekeying, Group Members respond to rekey messages by replying to the Key Server with an acknowledgement.
If the Key Server does not receive acknowledgements for three consecutive rekey messages, it ejects that Group Member from the VPN, forcing it to reregister in order to resume sending encrypted traffic.
Multicast rekeying occurs 90 seconds prior to the SA expiration, and the rekey transmit time and rekey transmit number parameters are used to control how often and for how long the rekey messages will be transmitted. This is done to counter unexpected or intermittent packet loss, since Group Members do not acknowledge the receipt of multicast rekey messages.
Anti-Replay
Anti-replay mechanisms are used to prevent the retransmission of traffic captured in transit by a third party. GET-VPN can discard packets suspected of being replayed using either of two methods – counter-based and time-based.
Counter-based
Counter-based anti-replay uses a sliding window based on the sequence number of the arriving packets. If the sequence number of a packet is outside of the lower window boundary, it is considered to be a replayed packet and is discarded.
The use of counter-based anti-replay is common in tunnel-based VPNs, where there is a single pair of endpoints that packets travel between, providing a consistent parade of sequence numbers.
Time-based
Since counter-based anti-replay is of limited use in a tunnel-less environment, GET-VPN also offers anti-replay protection based on timestamp values using a mechanism called Synchronous Anti-Replay (SAR).
SAR is a GET-VPN-specific clocking function that is not dependent on the router’s time setting or on connectivity to an NTP source. The SAR clock runs continuously and tracks “pseudotime” in seconds, beginning with the successful registration of the first Group Member. The “authoritative” pseudotime is maintained by the Key Server and the current pseudotime value is periodically sent to the Group Members within a rekey message, effectively synchronizing the VPN.
The current pseudotime value is included with each encrypted packet that is created by a Group Member. When the packet arrives at the receiving Group Member, it compares the pseudotime value contained in the packet (the “pseudoTimeStamp”) with the running pseudotime value that it is maintaining. If the pseudoTimeStamp of the packet and the Group Member pseudotime are within the configured anti-replay window, then the packet is accepted.
CONFIGURATION
IKE Phase 1 Policy Commands using preshared key
crypto isakmp policy [IKE-Priority]
encryption [IKE-Encryption]
hash [IKE-Hash-Algorithm]
authentication pre-shared
group [IKE-DH-Group]
lifetime [IKE-SA-Lifetime]
crypto isakmp key 0 [KEY] address [GroupMember-IP-Address]
Key Server Configuration Commands
crypto key generate rsa label [NAME] modulus [MODULUS] (exportable)
crypto isakmp policy [IKE-Priority]
encryption [IKE-Encryption]
hash [IKE-Hash]
authentication pre-share
group [IKE-DH-Group]
lifetime [IKE-SA-Lifetime]
crypto isakmp key 0 [KEY] address [GroupMember]
crypto ipsec transform-set [NAME] [KEY] [HASH]
crypto ipsec profile [NAME]
set transform-set [NAME]
ip access-list extended [NAME]
permit [protocol] [source] [destination]
crypto gdoi group [NAME]
identity number [ID]
server local
rekey algorithm [TYPE]
rekey lifetime seconds [Lifetime]
rekey retransmit [TIME] number [NUMBER]
rekey authentication mypubkey rsa [RekeyNAME]
rekey transport unicast
registration interface [NAME]
address ipv4 [KeyServer]
sa ipsec [NUMBER]
profile [NAME]
match address ipv4 [NAME]
replay time window-size [SIZE]
Group Member Configuration Commands
crypto isakmp key 0 [Key] address [KeyServer]
crypto gdoi group [NAME]
identity number [Number]
server address ipv4 [KeyServer]
crypto map [NAME] [Sequence] gdoi
set group [NAME]
interface [WAN]
crypto map [NAME]
interface [WAN]
ip mtu 1480
Case Study
Key Server 1: Example
Key server 1 is the primary key server.
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service internal
hostname KS1
!
logging buffered 100000 debugging
no logging console
!
no aaa new-model
!
clock timezone EST 0
ip subnet-zero
no ip domain lookup
ip domain name cisco.com
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 400
crypto isakmp key cisco address 10.1.1.13
crypto isakmp key cisco address 10.1.1.9
crypto isakmp key cisco address 10.1.1.1
crypto isakmp key cisco address 10.1.1.5
crypto isakmp key cisco address 10.1.1.21
!
crypto ipsec transform-set gdoi-trans-group1 esp-3des esp-sha-hmac
!
crypto ipsec profile gdoi-profile-group1
set security-association lifetime seconds 1800
set transform-set gdoi-trans-group1
!
crypto gdoi group group1
identity number 1
server local
rekey lifetime seconds 86400
rekey retransmit 10 number 2
rekey authentication mypubkey rsa group1-export-general
rekey transport unicast
sa ipsec 1
profile gdoi-profile-group1
match address ipv4 101
replay counter window-size 64
address ipv4 10.1.1.17
redundancy
local priority 10
peer address ipv4 10.1.1.2
!
interface Ethernet0/0
ip address 10.1.1.17 255.255.255.252
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.1.1.18
!
access-list 101 permit ip 10.1.0.0 0.0.255.255 10.1.0.0 0.0.255.255
!
end
Key Server 2: Example
Key Server 2 is the secondary key server.
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service internal
!
hostname KS2
!
logging buffered 100000 debugging
no logging console
!
no aaa new-model
!
resource policy
!
clock timezone EST 0
ip subnet-zero
no ip domain lookup
ip domain name cisco
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 400
crypto isakmp key cisco address 10.1.1.9
crypto isakmp key cisco address 10.1.1.1
crypto isakmp key cisco address 10.1.1.5
crypto isakmp key cisco address 10.1.1.17
crypto isakmp key cisco address 10.1.1.13
!
crypto ipsec transform-set gdoi-trans-group1 esp-3des esp-sha-hmac
!
crypto ipsec profile gdoi-profile-group1
set security-association lifetime seconds 1800
set transform-set gdoi-trans-group1
!
crypto gdoi group group1
identity number 1
server local
rekey lifetime seconds 86400
rekey retransmit 10 number 2
rekey authentication mypubkey rsa group1-export-general
rekey transport unicast
sa ipsec 1
profile gdoi-profile-group1
match address ipv4 101
replay counter window-size 64
address ipv4 10.1.1.21
redundancy
local priority 1
peer address ipv4 10.1.1.17
!
interface Ethernet0/0
ip address 10.1.1.21 255.255.255.252
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.1.1.22
!
access-list 101 permit ip 10.1.0.0 0.0.255.255 10.1.0.0 0.0.255.255
!
end
Group Member 1: Example
Group Member 1 is part of a GDOI group that correlates with a VPN with which these sites are a part.
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname GM1
!
resource policy
!
clock timezone EST 0
ip subnet-zero
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 3600
crypto isakmp key cisco address 10.1.1.17
crypto isakmp key cisco address 10.1.1.21
!
crypto gdoi group group1
identity number 1
server address ipv4 10.1.1.17
server address ipv4 10.1.1.21
!
crypto map map-group1 10 gdoi
set group group1
!
interface Ethernet0/0
ip address 10.1.1.1 255.255.255.252
crypto map map-group1
!
router bgp 1000
no synchronization
bgp log-neighbor-changes
network 10.1.1.0 mask 255.255.255.0
neighbor 10.1.1.2 remote-as 5000
no auto-summary
!
ip classless
!
End
Group Member 2: Example
Group Member 2 is part of a GDOI group that correlates with a VPN with which these sites are a part.
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
!
hostname GM2
!
clock timezone EST 0
ip subnet-zero
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 3600
crypto isakmp key cisco address 10.1.1.17
crypto isakmp key cisco address 10.1.1.21
!
crypto gdoi group group1
identity number 1
server address ipv4 10.1.1.17
server address ipv4 10.1.1.21
!
crypto map map-group1 10 gdoi
set group group1
!
interface Ethernet0/0
ip address 10.1.1.5 255.255.255.252
crypto map map-group1
!
router bgp 2000
no synchronization
bgp log-neighbor-changes
network 10.1.2.0 mask 255.255.255.0
neighbor 10.1.1.6 remote-as 5000
no auto-summary
!
ip classless
!
end
Group Member 3: Example
Group Member 3is part of a GDOI group that correlates with a VPN with which these sites are a part.
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname GM3
!
resource policy
!
clock timezone EST 0
ip subnet-zero
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 3600
crypto isakmp key cisco address 10.1.1.17
crypto isakmp key cisco address 10.1.1.21
!
crypto ipsec transform-set gdoi-trans-group1 esp-3des esp-sha-hmac
crypto gdoi group group1
identity number 1
server address ipv4 10.1.1.17
server address ipv4 10.1.1.21
!
crypto map map-group1 10 gdoi
set group group1
!
interface Ethernet0/0
ip address 10.1.1.9 255.255.255.252
crypto map map-group1
!
router bgp 3000
no synchronization
bgp log-neighbor-changes
network 10.1.3.0 mask 255.255.255.0
neighbor 10.1.1.10 remote-as 5000
no auto-summary
!
ip classless
!
end
Group Member 4: Example
Group Member 4 is part of a GDOI group that correlates with a VPN with which these sites are a part.
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname GM4
!
clock timezone EST 0
ip subnet-zero
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 3600
crypto isakmp key cisco address 10.1.1.17
crypto isakmp key cisco address 10.1.1.21
!
crypto gdoi group group1
identity number 1
server address ipv4 10.1.1.17
server address ipv4 10.1.1.21
!
crypto map map-group1 10 gdoi
set group group1
!
interface Ethernet0/0
ip address 10.1.1.13 255.255.255.252
crypto map map-group1
!
router bgp 4000
no synchronization
bgp log-neighbor-changes
network 10.1.4.0 mask 255.255.255.0
neighbor 10.1.1.14 remote-as 5000
no auto-summary
!
ip classless
!
end
For more Information on GET VPN:

No comments:
Post a Comment